Table of Contents

In the sprawling digital economy, convenience and speed are king. But this rapid expansion has fueled a parallel, shadow economy of online fraud. For businesses, the challenge is immense: how do you protect your platform from sophisticated botnets, coordinated fraud rings, and AI-driven attacks without alienating legitimate customers? In this high-stakes environment, the ability to identify malicious actors before they can strike is paramount.
This is where the IP Fraud Score emerges as a foundational, real-time intelligence signal in the global fight against digital crime. It acts as an instant background check on every connection, offering a powerful first line of defense.
What Is an IP Fraud Score?
At its core, an IP Fraud Score is a numerical rating, typically on a scale of 0 to 100, that quantifies the likelihood of a specific Internet Protocol (IP) address being associated with malicious or fraudulent activity. Think of it as a digital "credit score" for an IP address, assessing its trustworthiness based on a comprehensive analysis of its history, characteristics, and behavior.
The scale is simple to interpret:
- Low Scores (e.g., 0-10): Indicate a clean, trusted IP address with a low probability of fraud.
- High Scores (e.g., 70-100): Signal a high risk, suggesting the IP has been linked to suspicious activities.
This scoring system is a specific type of fraud score focused exclusively on internet protocol-related risk factors. It’s designed to help businesses filter out malicious actors before they can access a site, create a fake account, or complete a fraudulent transaction. One of its key advantages is that the analysis happens entirely behind the scenes, invisible to the end-user, and delivers results in real-time, making it a highly cost-effective and frictionless first line of defense.
It's crucial to understand that an IP Fraud Score is a tool for probabilistic risk assessment, not a definitive judgment. A high score doesn't mean an IP address is fraudulent, but that it exhibits characteristics commonly associated with known fraudulent activity. For example, a fraudster might use a VPN to hide their location, but so might a privacy-conscious customer.
How Is an IP Fraud Score Calculated?
The calculation of an IP Fraud Score is a sophisticated process driven by advanced algorithms and vast datasets. Fraud detection platforms operate massive data aggregation engines that continuously collect and analyze information from public sources, like DNS Blackhole Lists (DNSBL), and their own proprietary networks.
The accuracy of a score is directly proportional to the size, quality, and most critically, the refresh rate of these databases. In the dynamic world of cybercrime, where fraudsters can rotate through thousands of IPs in a single day, a database that is even a few hours old may be outdated. Leading services refresh their data hourly, or even in real-time, to keep pace. This data is then fed into machine learning models that analyze complex patterns and assign risk points to various factors.
IP Address History
The most heavily weighted component is the IP address's history and reputation - its digital rap sheet. An IP's reputation is built over time based on its past behavior and is assessed through several key lenses:
- Abuse Reports: Direct reports of an IP address being involved in spamming, hacking, or payment fraud will dramatically increase its risk score.
- Blacklist Status: The system checks if the IP is listed on reputable public or private blacklists, such as those maintained by Spamhaus or Project Honeypot. An appearance on these lists is a strong negative signal.
- Historical Behavior Patterns: Algorithms analyze past behavior for suspicious patterns, such as an abnormally high number of interactions with web servers (indicating bot activity) or an IP address being associated with an unusually high number of different devices and user accounts.
Geolocation and Risk Regions
The geographic location derived from an IP address provides crucial context for risk assessment. Scoring systems leverage this data in several ways:
- Location Mismatches: A significant discrepancy between the IP's location and the user's provided information is a classic fraud indicator. For example, if a customer's billing address is in New York, but the transaction originates from an IP in Vietnam, the system will flag this as high-risk.
- High-Risk Jurisdictions: Connections from countries or regions with a known high incidence of cybercrime will inherently receive a higher risk weighting.
- Impossible Travel: This rule flags scenarios where an account is accessed from geographically distant locations in a physically impossible timeframe, such as a login from London followed minutes later by one from Tokyo.
Proxy or VPN Usage
Fraudsters rely on tools that mask their true identity and location, making the detection of anonymizing services a cornerstone of IP risk analysis. The use of a proxy, VPN, or the Tor network is a significant risk factor that contributes points to the overall fraud score. Scoring systems also differentiate between the type of IP address. A datacenter IP, typical for servers and many VPNs, is considered inherently riskier for a user transaction than a residential IP, which is assigned by an ISP to a home user.
This creates a fundamental tension: the Proxy vs. Privacy Paradox. The very technologies that privacy-conscious individuals use to protect their data, such as VPNs, are the same ones exploited by fraudsters. A user who takes proactive steps to enhance their privacy is, by default, increasing their IP fraud score.
Why Is IP Fraud Score Important?
In an increasingly hostile digital environment, strategically implementing IP fraud scoring is a business imperative. It empowers organizations to proactively defend against threats, strengthen their security posture, and improve the experience for legitimate customers.
Preventing Online Fraud
The most direct benefit of IP fraud scoring is its ability to prevent financial losses by mitigating fraudulent activities in real-time. By flagging high-risk IPs at checkout, e-commerce businesses can automatically block purchases made with stolen credit cards, significantly reducing chargeback fraud. Beyond payments, it helps combat:
- Application Fraud: Prevents fraudsters from opening accounts with stolen or synthetic identities.
- Bonus Abuse: Detects schemes where users create thousands of accounts to abuse sign-up bonuses or free trials.
- Account Takeover (ATO): A sudden login from a high-risk IP in a different country is a strong indicator of an ATO attack. In one case, a company thwarted an ATO attempt by flagging simultaneous logins from three different high-risk datacenter IPs in Europe and North America on an account normally accessed from China, allowing them to immediately blacklist the IPs and secure the user's account.
Enhancing Cybersecurity
IP fraud scores are a critical data point that strengthens an organization's entire cybersecurity posture. Security teams can leverage IP risk data to trace the origin of phishing campaigns or unauthorized access attempts. By integrating this data into security infrastructure like firewalls, organizations can create dynamic blacklists that automatically block known malicious IPs at the network edge, preventing them from ever reaching sensitive applications.
Improving Customer Trust
A well-implemented fraud prevention system is a powerful tool for building customer trust. Research shows that data protection is a top concern for digital consumers, with 93% of digital banking users stating it is important or very important to them.
The strategic value of IP scoring lies in its ability to enable Dynamic Friction. This is the concept of applying security measures that are commensurate with the level of risk, rather than imposing a burdensome, one-size-fits-all approach.
- A user with a low-risk IP score can be automatically approved and enjoy a completely frictionless experience.
- A user with a medium-risk score can be presented with a "step-up" challenge, like a CAPTCHA or a one-time passcode, to verify their identity without being blocked.
- Only users with high-risk scores are subjected to the highest levels of friction, such as an automatic block or a mandatory manual review.
This adaptive model allows businesses to maintain robust security while providing the smoothest experience possible for the vast majority of their trusted users.
How to Check an IP Fraud Score
Accessing IP fraud score data can be done through manual lookups using online tools or through direct system integration via an API for automated prevention.
Using Online IP Scoring Tools
For quick checks or small-scale use, numerous online services offer free IP lookup capabilities. The process is typically straightforward:
1. Navigate to the tool's website, such as Scamalytics or IPQualityScore (in this example, we will show Scamalytics)
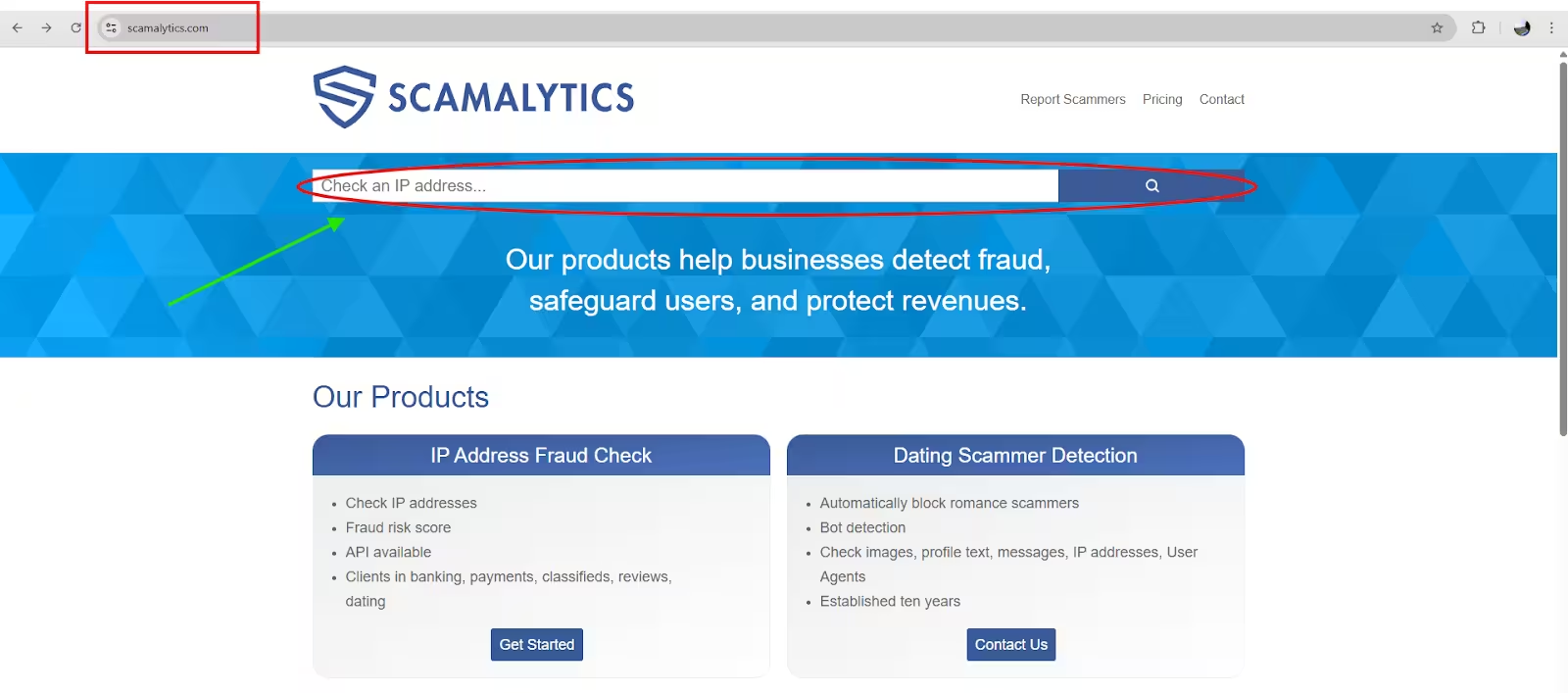
2. Enter the IP address you wish to investigate (red circle).

3. Execute the check to submit the query (green square).
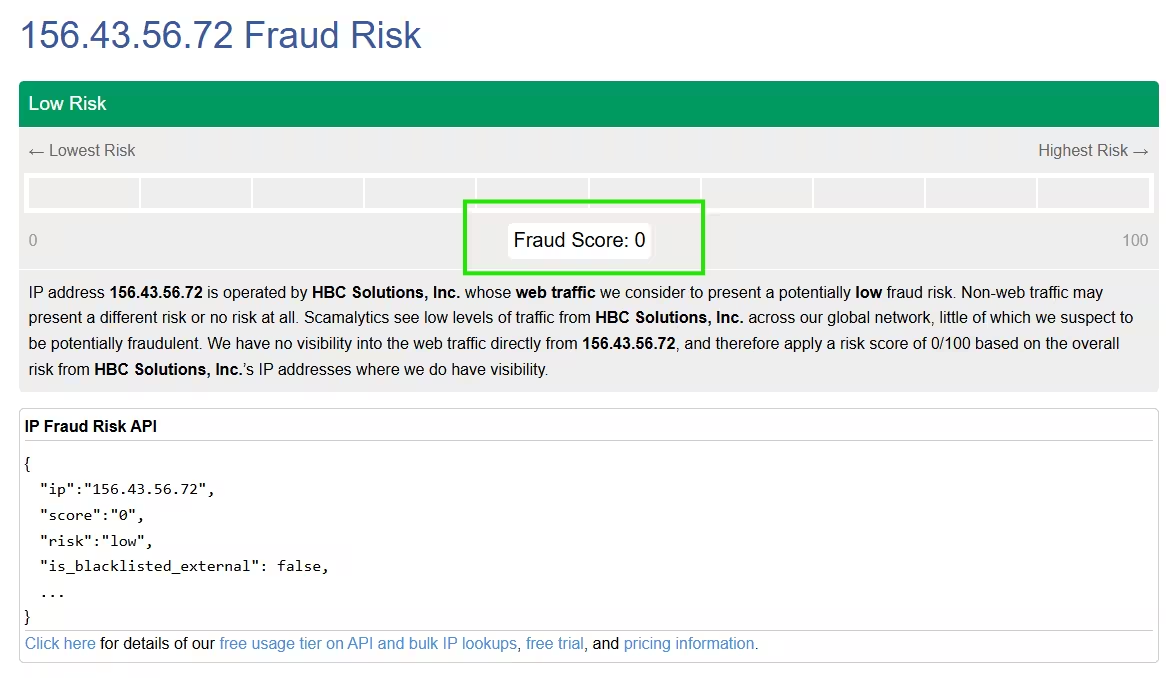
4. Review the results, which will contain the IP fraud score and associated data.
Integrating IP Fraud Scores in Business Systems
For any business operating at scale, manual lookups are impractical. Real-time, automated prevention requires integrating an IP scoring service directly into your systems via an Application Programming Interface (API). This allows every user action to be scored automatically.
The general process for API integration is as follows:
- Select a Provider and Get an API Key: Choose a service and register to receive a unique API key for authenticating your requests.
- Make API Calls: At critical touchpoints (e.g., checkout), your application's backend server makes a request to the provider's API, sending the user's IP address.
- Parse the API Response: The service instantly returns a structured data response, usually in JSON format, containing the fraud score and other details.
- Implement Business Logic: Your application code parses the response and triggers predefined rules. For example, if the fraud score is high, the code could automatically decline the transaction.